Time to examine for those who ran any of those 33 malicious Chrome extensions

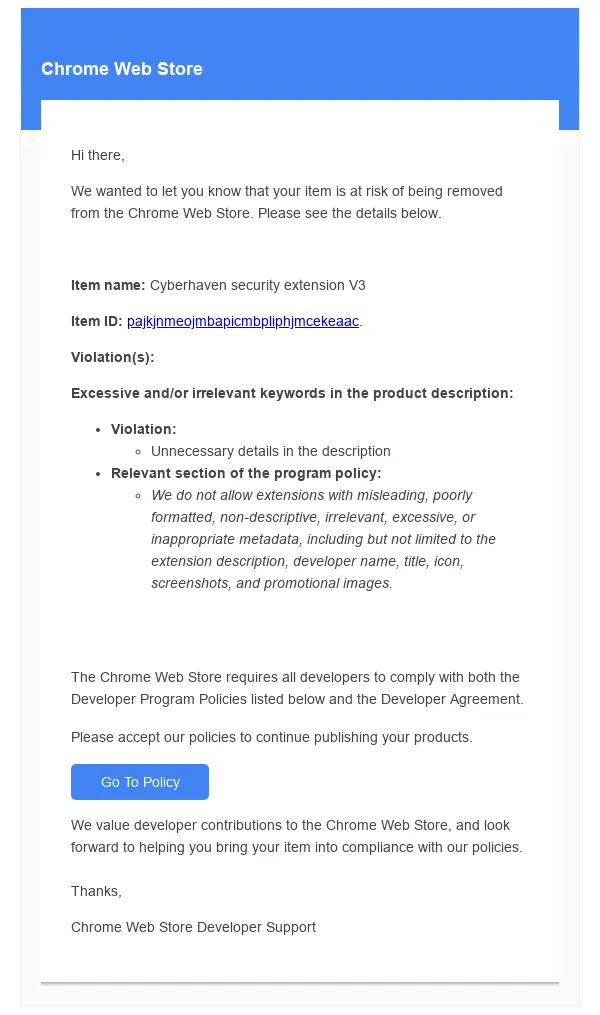
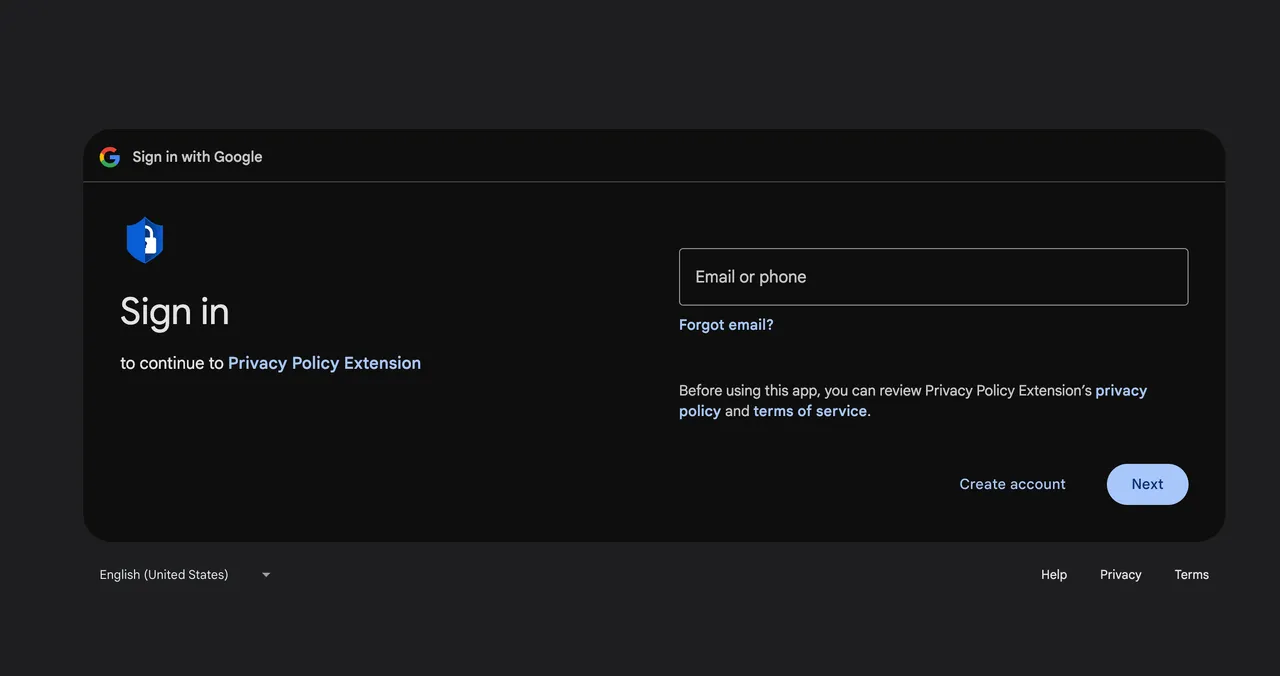
A hyperlink within the electronic mail led to a Google consent display requesting entry permission for an OAuth software named Privateness Coverage Extension. A Cyberhaven developer granted the permission and, within the course of, unknowingly gave the attacker the flexibility to add new variations of Cyberhaven’s Chrome extension to the Chrome Internet Retailer. The attacker then used the permission to push out the malicious model 24.10.4.
As phrase of the assault unfold within the early hours of December 25, builders and researchers found that different extensions have been focused, in lots of circumstances efficiently, by the identical spear phishing marketing campaign. John Tuckner, founding father of Safe Annex, a browser extension evaluation and administration agency, stated that as of Thursday afternoon, he knew of 19 different Chrome extensions that have been equally compromised. In each case, the attacker used spear phishing to push a brand new malicious model and customized, look-alike domains to difficulty payloads and obtain authentication credentials. Collectively, the 20 extensions had 1.46 million downloads.
“For a lot of I discuss to, managing browser extensions is usually a decrease precedence merchandise of their safety program,” Tuckner wrote in an electronic mail. “Of us know they’ll current a menace, however hardly ever are groups taking motion on them. We have typically seen in safety [that] one or two incidents may cause a reevaluation of a corporation’s safety posture. Incidents like this typically end in groups scrambling to discover a approach to achieve visibility and understanding of influence to their organizations.”
The earliest compromise occurred in Might 2024. Tuckner supplied the next spreadsheet:
| Identify | ID | Model | Patch | Accessible | Customers | Begin | Finish |
| VPNCity | nnpnnpemnckcfdebeekibpiijlicmpom | 2.0.1 | FALSE | 10,000 | 12/12/24 | 12/31/24 | |
| Parrot Talks | kkodiihpgodmdankclfibbiphjkfdenh | 1.16.2 | TRUE | 40,000 | 12/25/24 | 12/31/24 | |
| Uvoice | oaikpkmjciadfpddlpjjdapglcihgdle | 1.0.12 | TRUE | 40,000 | 12/26/24 | 12/31/24 | |
| Internxt VPN | dpggmcodlahmljkhlmpgpdcffdaoccni | 1.1.1 | 1.2.0 | TRUE | 10,000 | 12/25/24 | 12/29/24 |
| Bookmark Favicon Changer | acmfnomgphggonodopogfbmkneepfgnh | 4.00 | TRUE | 40,000 | 12/25/24 | 12/31/24 | |
| Castorus | mnhffkhmpnefgklngfmlndmkimimbphc | 4.40 | 4.41 | TRUE | 50,000 | 12/26/24 | 12/27/24 |
| Wayin AI | cedgndijpacnfbdggppddacngjfdkaca | 0.0.11 | TRUE | 40,000 | 12/19/24 | 12/31/24 | |
| Search Copilot AI Assistant for Chrome | bbdnohkpnbkdkmnkddobeafboooinpla | 1.0.1 | TRUE | 20,000 | 7/17/24 | 12/31/24 | |
| VidHelper – Video Downloader | egmennebgadmncfjafcemlecimkepcle | 2.2.7 | TRUE | 20,000 | 12/26/24 | 12/31/24 | |
| AI Assistant – ChatGPT and Gemini for Chrome | bibjgkidgpfbblifamdlkdlhgihmfohh | 0.1.3 | FALSE | 4,000 | 5/31/24 | 10/25/24 | |
| TinaMind – The GPT-4o-powered AI Assistant! | befflofjcniongenjmbkgkoljhgliihe | 2.13.0 | 2.14.0 | TRUE | 40,000 | 12/15/24 | 12/20/24 |
| Bard AI chat | pkgciiiancapdlpcbppfkmeaieppikkk | 1.3.7 | FALSE | 100,000 | 9/5/24 | 10/22/24 | |
| Reader Mode | llimhhconnjiflfimocjggfjdlmlhblm | 1.5.7 | FALSE | 300,000 | 12/18/24 | 12/19/24 | |
| Primus (prev. PADO) | oeiomhmbaapihbilkfkhmlajkeegnjhe | 3.18.0 | 3.20.0 | TRUE | 40,000 | 12/18/24 | 12/25/24 |
| Cyberhaven safety extension V3 | pajkjnmeojmbapicmbpliphjmcekeaac | 24.10.4 | 24.10.5 | TRUE | 400,000 | 12/24/24 | 12/26/24 |
| GraphQL Community Inspector | ndlbedplllcgconngcnfmkadhokfaaln | 2.22.6 | 2.22.7 | TRUE | 80,000 | 12/29/24 | 12/30/24 |
| GPT 4 Abstract with OpenAI | epdjhgbipjpbbhoccdeipghoihibnfja | 1.4 | FALSE | 10,000 | 5/31/24 | 9/29/24 | |
| Vidnoz Flex – Video recorder & Video share | cplhlgabfijoiabgkigdafklbhhdkahj | 1.0.161 | FALSE | 6,000 | 12/25/24 | 12/29/24 | |
| YesCaptcha assistant | jiofmdifioeejeilfkpegipdjiopiekl | 1.1.61 | TRUE | 200,000 | 12/29/24 | 12/31/24 | |
| Proxy SwitchyOmega (V3) | hihblcmlaaademjlakdpicchbjnnnkbo | 3.0.2 | TRUE | 10,000 | 12/30/24 | 12/31/24 |
However wait, there’s extra
One of many compromised extensions known as Reader Mode. Additional evaluation confirmed it had been compromised not simply within the marketing campaign concentrating on the opposite 19 extensions however in a separate marketing campaign that began no later than April 2023. Tuckner stated the supply of the compromise seems to be a code library builders can use to monetize their extensions. The code library collects particulars about every internet go to a browser makes. In alternate for incorporating the library into the extensions, builders obtain a fee from the library creator.







